 |
 |
 |
|
 |
|||
| RE 1: Investigating User Demand |
 RE1 - Erhebung des Anwenderbedarfs
RE1 - Erhebung des Anwenderbedarfs
 Contents Contents
|
|
|---|
 Product Flow
Product Flow
| From | Product | to | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Activity | State | Chapter | Title | Activity | State | ||||||||||||
| External (1) | - | All | Existing source code | - | -
| External (1) |
- |
All |
Further information (2) |
- |
-
| - |
- |
All |
User Demand |
RE2 |
RE3 RE4 RE8 External (1) submitted
| |
 Handling
Handling
(start daVinci Graph Visualization Tool v2.0)
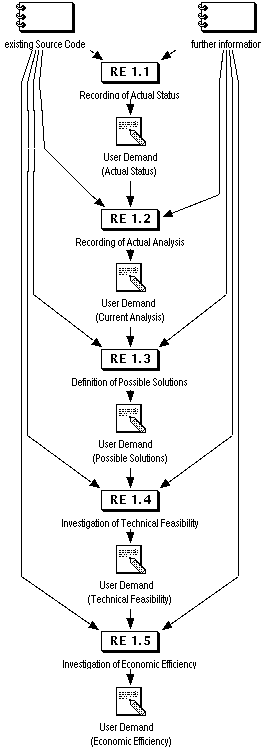
Figure RE 1: Investigating User Demand
When specifying the User Demand, the actual state of the existing source code and all other available/existing system and software documentation can be used and analyzed in order to find out possible weak points with regard to aspects of reverse engineering. Solutions will be defined for the detected weak points. The technical feasibility and economic efficiency of the defined solutions will be investigated.
 Sub-activities
Sub-activities
RE 1.1: Recording of Actual Status RE 1.2: Recording of Current Analysis
RE 1.3: Definition of Possible Solutions
RE 1.4: Investigation of Technical Feasibility
RE 1.5: Investigation of Economic Efficiency
Notes (1) Customer
(2) Other system and software documentation and all other available information.
 |
 |
 GDPA Online
GDPA Online
 Last Updated 01.Jan.2002 Last Updated 01.Jan.2002
 Updated by Webmaster Updated by Webmaster
 Last Revised 01.Jan.2002 Last Revised 01.Jan.2002
 Revised by Webmaster Revised by Webmaster
 |